A few days ago, a friend asked me to help with an exam software. After checking, it was protected by Enigma Protector and required an license file/key…
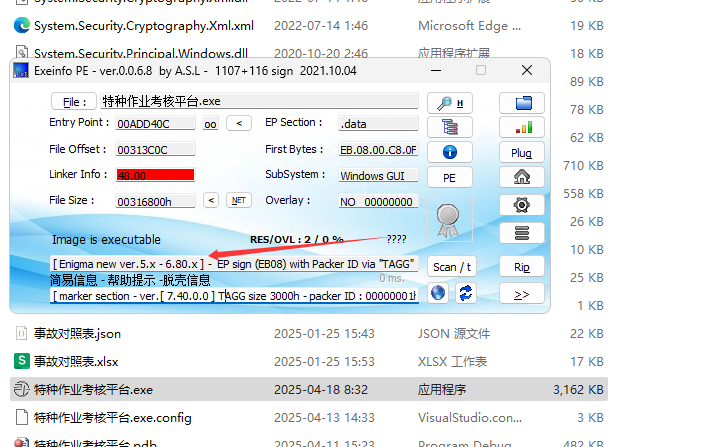
I put this main PE file into the ExeInfo PE tool for inspection.
info:
When running it, a registration box for the license key appeared, and my machine code was displayed.
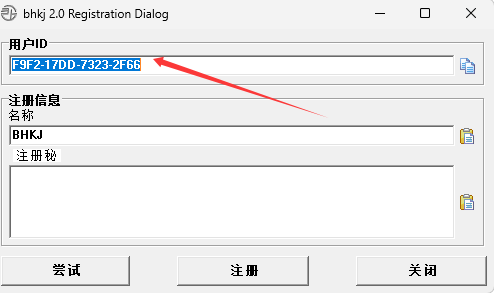
In the absence of a key, I had no choice but to resort to more brute-force methods.
Since Enigma Protector is written in Delphi, the license registration form can also be analyzed using Delphi program code analysis techniques.
Load OllyDbg and set an int3 breakpoint at GetWindowTextW, then check the stack.
0145FA2C 006E5A75 /CALL to GetWindowTextW from 特种作业.006E5A70
0145FA30 03AF11D2 |hWnd = 03AF11D2 (class='TEnigmaProtectorLoaderRegistr...')
0145FA34 015DD41C |Buffer = 015DD41C
0145FA38 00000001 \Count = 0x1
0145FA3C 0145FA70 Pointer to next SEH record
0145FA40 006E5AB1 SE handler
0145FA44 0145FA68
0145FA48 03F03C98
0145FA4C 015FCC64 UNICODE "%AppName% %AppVers% Registration Dialog"
0145FA50 03F03C98
0145FA54 00000000
0145FA58 00000000
0145FA5C 00000000
0145FA60 00000000
0145FA64 00000000
0145FA68 /0145FA94
0145FA6C |006E5B8B RETURN to 特种作业.006E5B8B from 特种作业.006E5950
0145FA70 |0145FA9C Pointer to next SEH record
0145FA74 |006E5BE4 SE handler
0145FA78 |0145FA94
0145FA7C |03F02D0C ASCII "%AppName% %AppVers% Registration Dialog"
0145FA80 |03F03C98
0145FA84 |03F06F94
0145FA88 |015DD41C ASCII "sQ"
0145FA8C |00000000
0145FA90 |00000000
0145FA94 ]0145FABC
0145FA98 |006E6205 RETURN to 特种作业.006E6205 from 特种作业.006E5AC0
0145FA9C |0145FAD4 Pointer to next SEH record
0145FAA0 |006E6220 SE handler
0145FAA4 |0145FABC
0145FAA8 |0145FBCC
0145FAAC |03F02D0C ASCII "%AppName% %AppVers% Registration Dialog"
0145FAB0 |03F06F94
0145FAB4 |015FCED4 UNICODE "%AppName% %AppVers% Registration Dialog"
0145FAB8 |015FCC64 UNICODE "%AppName% %AppVers% Registration Dialog"
After tracing back the stack information for some time and ctrl+F9 you’ll reach the point where the registration form is created.

0064CA79 5F POP EDI
0064CA7A 5E POP ESI
0064CA7B 5B POP EBX
0064CA7C 8BE5 MOV ESP, EBP
0064CA7E 5D POP EBP
0064CA7F C3 RETN ///Return to 00CBA379
00CBA379 68 74A57AC2 PUSH 0xC27AA574 ; Form
00CBA37E ^ E9 B176ACFF JMP 00781A34
00CBA383 68 77A57AC2 PUSH 0xC27AA577 ..........
00CBA388 ^ E9 A776ACFF JMP 00781A34
00CBA38D 68 44A57AC2 PUSH 0xC27AA544
Trace this address 00CBA379 until the window runs.
00781A34 60 PUSHAD
00781A35 9C PUSHFD
00781A36 B2 01 MOV DL, 0x1
006B8790 5B POP EBX
006B8791 C3 RETN //Return to 00CBA383
Enter the account “Sound” (5 digits) and the key “1234567890” (10 digits).

Click the registration button and set a breakpoint at 00781A34. Then use Execute till Return to trace to.(Check the stack. First, the username Sound is retrieved)
0145E6C0 C27A82B3
0145E6C4 0145E6F0
0145E6C8 0145EA40 Pointer to next SEH record
0145E6CC 00CC00F2 SE handler
0145E6D0 0145E6F0
0145E6D4 03D76A30 ASCII "x衬"
0145E6D8 00000000
0145E6DC 00000000
0145E6E0 017DCD8C UNICODE "123456789"
0145E6E4 09AF3EAC UNICODE "Sound"
0145E6E8 00000000
0145E6EC 09AF3BDC UNICODE "Sound"
0145E6F0 /0145E830
The password is then retrieved, and the debugger continues tracing until the accumulator register EAX contains the concatenated lengths of Sound and 123456789.
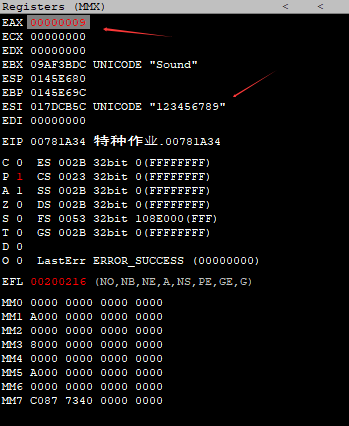
0145E6C4 C27A82BF
0145E6C8 0145EA40 Pointer to next SEH record
0145E6CC 00CC00F2 SE handler
0145E6D0 0145E6F0
0145E6D4 03D76A30 ASCII "x衬"
0145E6D8 00000000
0145E6DC 00000000
0145E6E0 017DCD8C UNICODE "123456789"
0145E6E4 09AF3EAC UNICODE "Sound"
0145E6E8 017DCB5C UNICODE "123456789"
0145E6EC 09AF3BDC UNICODE "Sound"
Execute till Return
00CB2DC1 68 50F37AC2 PUSH 0xC27AF350 ; EAX=9
00CB2DC6 ^ E9 69ECACFF JMP 00781A34
00CB2DCB 68 5DF37AC2 PUSH 0xC27AF35D ; EAX=5
00CB2DD0 ^ E9 5FECACFF JMP 00781A34Set breakpoints at the two addresses above and examine the stack. You’ll find operations involving the username and the computed registration code.
0145E514 03E04D60 ASCII "123456789"
0145E518 00000009
0145E51C 0145E560 Pointer to next SEH record
0145E520 00CBDF52 SE handler
0145E524 0145E534
0145E528 019228D4 UNICODE "Sound"
0145E52C 019225DC UNICODE "123456789"
0145E530 03E04D60 ASCII "123456789"
0145E534 0145E550
0145E538 00CB3C19 特种作业.00CB3C19 // Here
0145E53C 019228D4 UNICODE "Sound"
0145E540 0184BC14 UNICODE "123456789"
0145E544 0145E714
0145E548 006B2D20 特种作业.006B2D20
Set a breakpoint directly here 00CB3C19 . When execution hits this point, modify the value of the accumulator register (EAX) to 1.

Run the program. Once the main interface appears, remove all breakpoints.
Reload the debugger and set a breakpoint at VirtualAlloc.
After hitting the VirtualAlloc breakpoint, set a second breakpoint at 00CB3C19.
When execution pauses at 00CB3C19, modify EAX to 1.
Observe that the license protection is bypassed by click registration.. .. 🙂
BTW:When using the license protect function of enigma. We need to set the relevant options.(encrypt application with encryption constant) and (protection features > inline patching )
Leave a Reply